Encryption is an unbelievably complicated topic and I’m only now beginning to get comfortable with digital signatures in Office documents.
The Good News is that in Office 2007, other than the fact that the menu locations for checking signatures has changed, most everything about digital signatures has remained the same as in Office 2003, and, from what I can tell, things are compatible all the way back to Office 2000.
The Bad News is that it’s still complicated as hell to deal with digital signatures.
I’ll try to cover a few of the bigger bits I’ve come up against while digging through digital signatures in Office (and in particular, in Word).
Signing a DOT file
The first thing you must do when getting ready to sign a template is to manually enable timestamping. Ok, technically, you don’t have to do this, but if you don’t timestamp the signature, when the certificate used to sign the template expires, so will the signature, and poof, your template will no longer be signed. Depending on how the user’s Word Is configured, that may mean that your template now fails to load.
You enable timestamping by adding a few entries to the registry. Office doesn’t provide a way to do this via the UI (even in 2007), so it’s all regedit (or run the REG script below).
Windows Registry Editor Version 5.00
[HKEY_CURRENT_USER\Software\Microsoft\VBA\Security]
“TimeStampURL”=”http://timestamp.verisign.com/scripts/timstamp.dll“
“TimeStampRetryCount”=dword:00000005
“TimeStampRetryDelay”=dword:00000005
Once you’ve turned timestamping on, you need to verify that you have a digital certificate loaded that can be used to sign templates.
Click the Start button and RUN, enter MMC and press Enter. This should bring up an empty Management Console.

Click FILE, Add/Remove Snap-in and find the Certificates snap in, then load it up.
When it asks for what type of certificates to manage, select the computer account.

Next, it should ask about managing the local computer account or a remote computer account. You’ll normally want to only deal with the Local Computer.
Once you get the certificate manager loaded, expand the personal certificates. Generally speaking, this is where certificates purchased through online vendors (like Verisign) will end up when you download them.
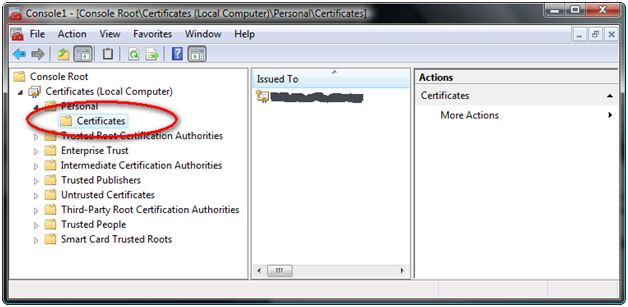
Now, right click the certificate and choose Properties.

You should see code signing in the box as shown. I’m not an expert on the different types of certificates, so it may be possible to sign documents WITHOUT a code signing certificate. Best to talk with someone at your vendor for details on that. One definite benefit of a code signing cert is that you can use it to sign DLLs, and EXEs, as well as templates.
Anyway, at this point, you can be pretty sure the cert is appropriate for signing templates.
One final note: It is often a good idea to export the signature so you can use it via the command line etc. The PFX (Personal Information Exchange) file format is good for this, because it contains both the public and private keys for the certificate. The bad news is you want to protect the PFX file as much as possible, because if someone obtains it and the password used to create it, they would be able to sign documents as if they were you.
You can export to a PFX file by right clicking the certificate entry (in the middle list), selecting All Tasks, then Export.
Indicate that you want to export the private key (which will require a password), and then make sure you select the PFX output option.
Verifying the Signature
Verifying that you actually got the Digital Signature correct is one of the more frustrating parts of working with digital signatures in Office.
You’d think you’d be able to verify the signature via the Tools/Digital Signatures menu in the VBA editor screen:




If you get this far, you know that the signature was signed. You can check the valid dates on the certificate as well.
However, this screen does NOT show the date the signature was timestamped and that, unfortunately, is a key piece of information you need to verify the signature. In fact, although this screen purports to be showing the digital signature, this is really just information on the certificate used to create the signature.
Verifying the TimeStamp
To actually get information about the signature, and specifically the timestamp, you have to jump through a few hoops.
First, make sure that the template IS NOT in any of the autoload places (most commonly the Word STARTUP folder or the Excel XLSTART folder).
Next, make sure that security is set such that unsigned templates won’t automatically load without prompting.



Once you’ve done that, if you put the signed template, say, on the desktop and load it by holding down the SHIFT key, right clicking, and selecting OPEN, you should get the message bar indicating that there are security warnings.

Click the Options button and you should get a Security Alerts Window:

Click the Show Signature Details link to see the actual details of the signature itself:

Notice the title of this dialog is actually “Digital Signature Details”, not “Certificate Details”. And the Signing Time is indicated here, showing that, in fact, this digital signature was timestamped.
One final note. The Office 2007 and 2003 object model (and XP, but not Office 2000), contains properties for enumerating and retrieving information on document and template signatures. Specifically, the DOCUMENT object now sports a SignatureSet property, which is a collection of signatures on the document. From there, you can navigate through the object model to retrieve all the signatures on the document, as well as details (including the signing time) of those signatures.
However, there are significant differences between the models in 2007 vs 2003, so any code written to utilize those objects would need to accommodate those differences.
The above steps work similarly in all versions of Office from 2000 to 2007. I’ll try to capture screenshots of the process in Word 2000 at some point, to illustrate the differences.
Related links
Office 2000 Macro Security